IDENTIFYING PHISHING AND SPOOFING ATTACK IN THE CYBERSPACE
In today’s digital age, where the internet is an integral part of our lives, it’s crucial to know how to protect yourself from cyber threats like phishing and spoofing attacks. These attacks aim to trick you into revealing sensitive information, such as passwords, credit card details, or personal data. In this guide, we’ll break down the basics of identifying phishing and spoofing attacks in simple terms. You don’t need to be a tech expert to stay safe – just a few key insights can go a long way in keeping your online experiences secure. Let’s dive in and empower you to navigate the vast cyberspace with confidence!
Phishing and spoofing are both cyberattack techniques used to deceive individuals or organizations, often with malicious intent. While they are related and can sometimes overlap, they refer to slightly different aspects of cyber deception:
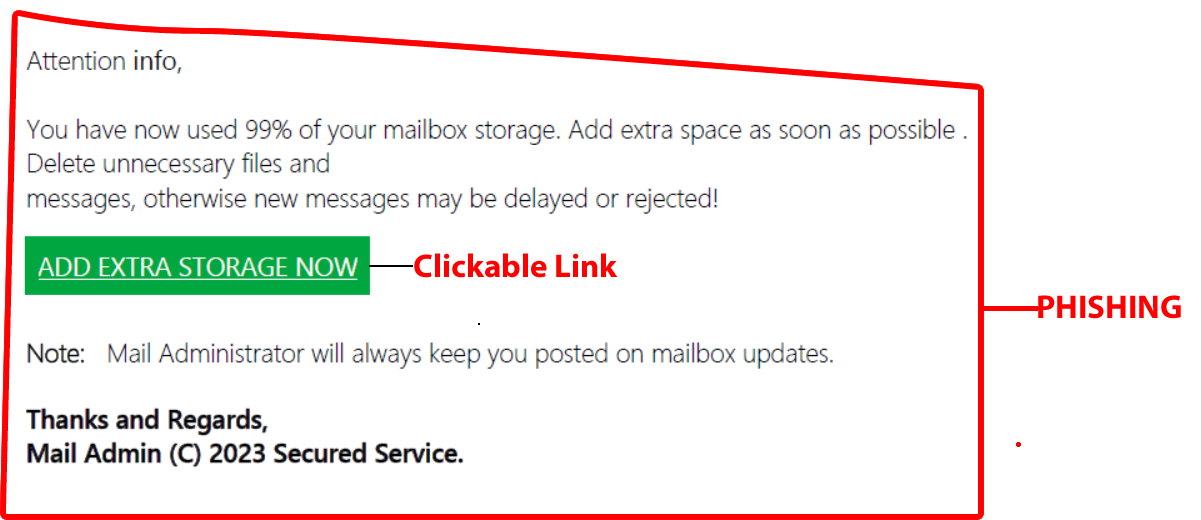
Phishing: Phishing is a method in which attackers use fraudulent emails, messages, or websites to trick individuals into revealing sensitive information, such as usernames, passwords, credit card numbers, or other personal data. These emails or messages often appear to come from legitimate sources, such as banks, social media platforms, or reputable companies. Phishing attempts often include urgent or enticing language to manipulate recipients into taking action without thinking.
For example, a phishing email might ask you to click on a link to update your account information, but the link actually leads to a fake website designed to capture your login credentials.
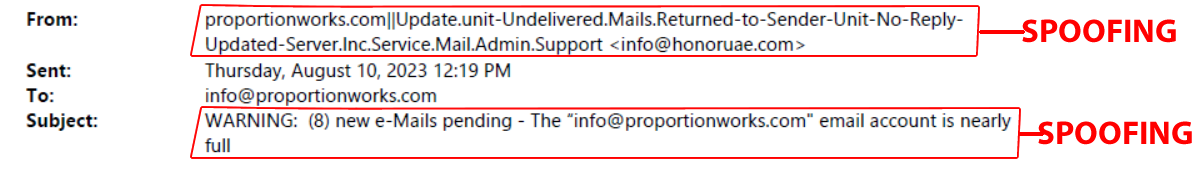
Spoofing: Spoofing, on the other hand, involves manipulating the source of communication to make it appear as though it’s coming from a legitimate or trusted entity, even when it’s not. This can apply to various forms of communication, such as emails, websites, phone calls, or IP addresses. Spoofing doesn’t necessarily involve deception to the same degree as phishing; it’s more about disguising the origin of the communication.
For instance, email spoofing involves forging the sender’s email address to make it look like the email is coming from a trusted source, even though it might be sent by a malicious actor.
Protecting Yourself
Now that we’ve shed light on phishing and spoofing attacks, let’s discuss how you can protect yourself, especially if you’re new to the online landscape:
- Stay Skeptical: Always be cautious of unexpected emails, messages, or calls that ask for personal information. If something seems urgent or too good to be true, take a step back and verify the legitimacy through official channels.
- Double-Check URLs: Before clicking on any links, hover your cursor over them to see where they lead. If the URL looks suspicious or doesn’t match the official website, avoid clicking.
- Verify Identities: If you receive an email or message from someone you know but the content seems unusual, reach out to them through a different channel to confirm their request.
- Use Security Software: Install reputable antivirus and antimalware software on your devices to help identify and prevent potential threats.
- Educate Yourself: Keep learning about the latest phishing and spoofing techniques. Stay informed about common tactics used by cybercriminals.
- Enable Multi-Factor Authentication (MFA): Whenever possible, activate MFA for your online accounts. This adds an extra layer of security by requiring a second form of verification, like a text message code, in addition to your password.
CONCLUSION
In summary, while phishing focuses on tricking individuals into divulging sensitive information through deceptive messages or websites, spoofing is about manipulating the source of communication to appear legitimate, which can facilitate various types of cyberattacks, including phishing. Both techniques are used to exploit human psychology and trust in order to gain unauthorized access to personal information or networks.